Industry 4.0 – New Avenue for Cyberattacks; is Asia Ready?
|
Smart factories and digital supply chains have become a growing trend in global business and trade, signalling the era of modern manufacturing and Industry 4.0, the fourth industrial revolution. Modern manufacturing is marked by the emergence of technologies such as cyber-physical systems, the Internet of Things (IoT), cloud computing, and cognitive computing. Industry 4.0 initiatives generated roughly USD 5.1 billion in 2017, and the figure is expected to grow at a CAGR of roughly 20–25% over 2017–25E to reach USD 21.7 billion. |
|
Nevertheless, growing interconnectivity and digitisation along company value chains could increase the threat of cyberattacks on the industry. Cybercrimes are already known to be the third-largest form of crime, (behind government corruption and narcotics) and in 2017, global cybercrime costs accounted for 0.8% of global GDP, with the Asia-Pacific region accounting for approximately 30% of global cybercrime costs. The risk of cyberattacks is expected to rise alongside the progression of Industry 4.0 in Asia. As per AT Kearney, hackers could target Asia specifically, owing to the region’s unsecured infrastructure compared with the North American and EU markets. Despite its prominence in Industry 4.0, we believe Asia would need to take several initiatives to fend off cyberthreats, including working closely with information security providers. Information security spend in Asia is expected to be among the highest globally. |
|
We believe that information security providers could therefore be one segment of potential beneficiaries of Industry 4.0. IoT security expenditure in the Asia-Pacific region is estimated to grow 2x over 2017–23E, as companies that adopt digitisation under Industry 4.0 would need to increasingly counter cybercrime activities. Among information security providers, in our view, the companies that stand to benefit the most are those that provide complete solutions across the value chain (i.e. product design/development and services), such as Cisco and other globally leading players. However, experts suggest that market competition could increase over the next 3–5 years alongside industry growth, as smaller players could enter the market and challenge the existing industry leaders. |
|
Evolution of Industry 4.0 and Its Potential Vulnerability to Cybercrime |
|
The phenomenon known as ‘Industry 4.0’ is the next phase in modern manufacturing. As the Internet of Things (IoT) develops further, physical devices at industrial/manufacturing plants are being linked to the Internet, allowing further automation of manufacturing processes. Such “smarter” manufacturing plants and the ability for physical devices (e.g. vendor devices, production machinery, logistic vehicles, etc.) to communicate with each other and trigger actions with minimal human involvement mean increased manufacturing efficiency. Industry 4.0 should lead to the emergence of digital manufacturing, characterised by smart networking, mobility, flexibility within industrial operations, and the integration of customers and innovative business models. For all its benefits, however, the increasing interconnectedness of the Digital Service Network also brings with it cyber weaknesses that should be properly planned for and accounted for at every stage, from design through operation, to curb significant risks. Any increased incidence of cybercrime could lead to revenue losses, downturns in profit, and irreparable brand damage and pose a significant threat to people and assets. |
|
One of the key challenges for cybersecurity at manufacturing plants is the difficulty of identifying attacks in operational technology (OT) environments. For instance, consider a plant where a component in the plant’s machinery suddenly stopped working, for unknown reasons. The chances are that a cyber attack is not going to be the workers’ first consideration when trying to figure out what went wrong; rather, they would tend to allude the breakdown to a technical fault, which it could be in most cases. However, as manufacturing plants become smarter, organisations may have to look deeper for root causes of breakdowns, considering the growing risk of cyber attacks. Although monitoring services exist for OT environments, they have limited application due to the necessity for network zones, or segmentation (sensors need to be placed at several different layers within a network). |
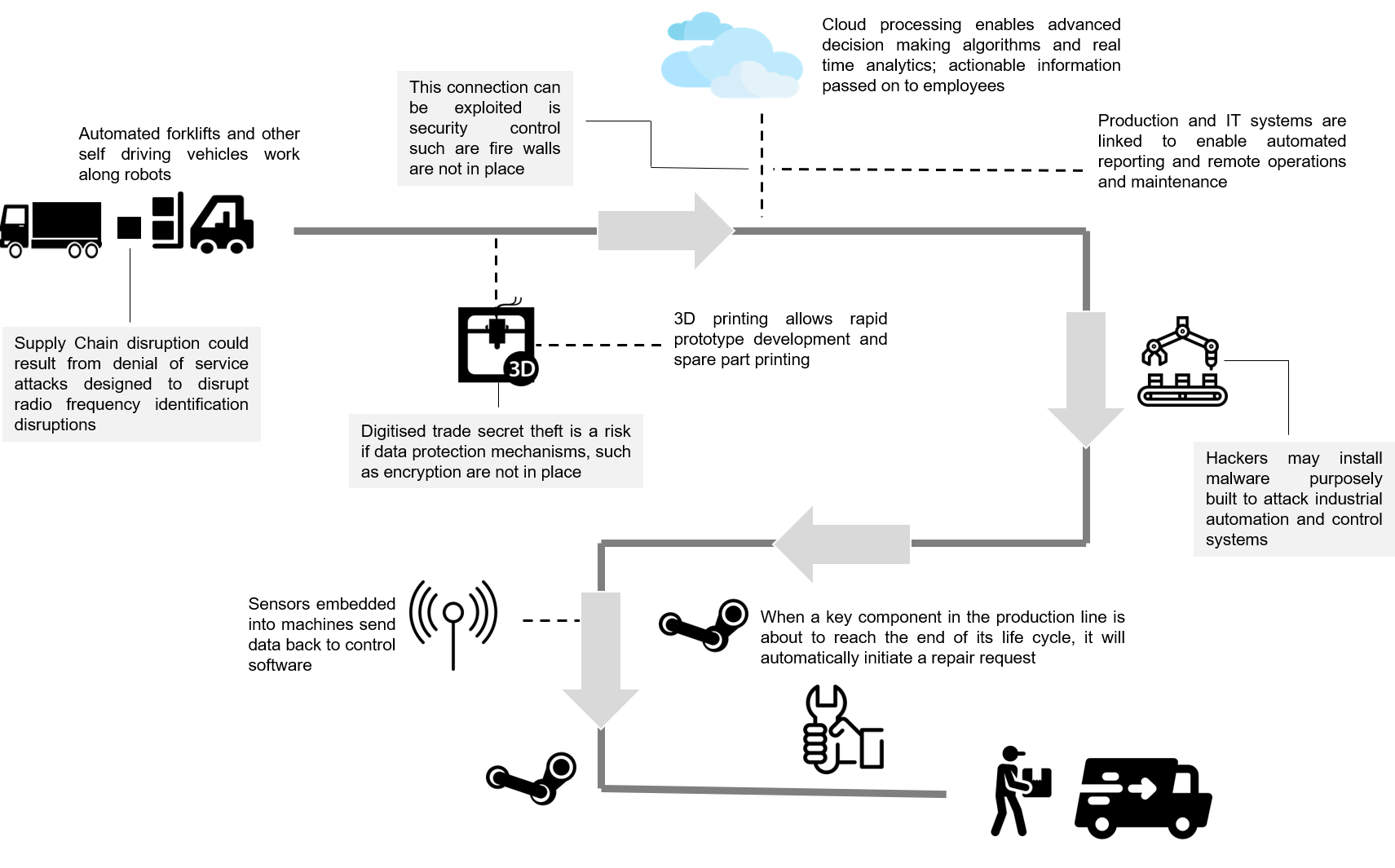 |
|
Source: Created by UZABASE based on various materials |
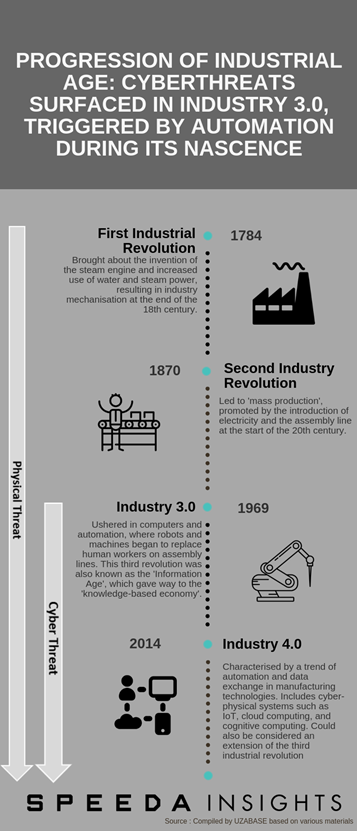 |
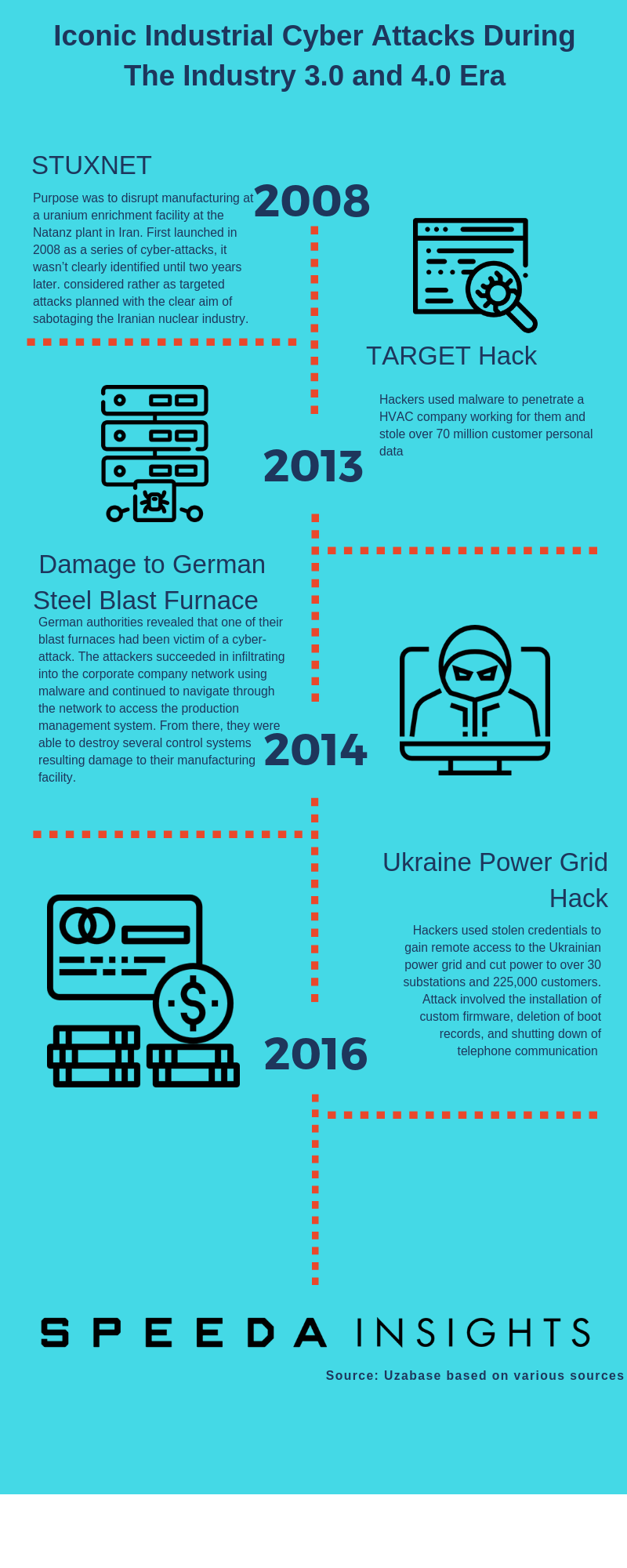 |
|
Industry 4.0 to Take Centre Stage in Asia |
|
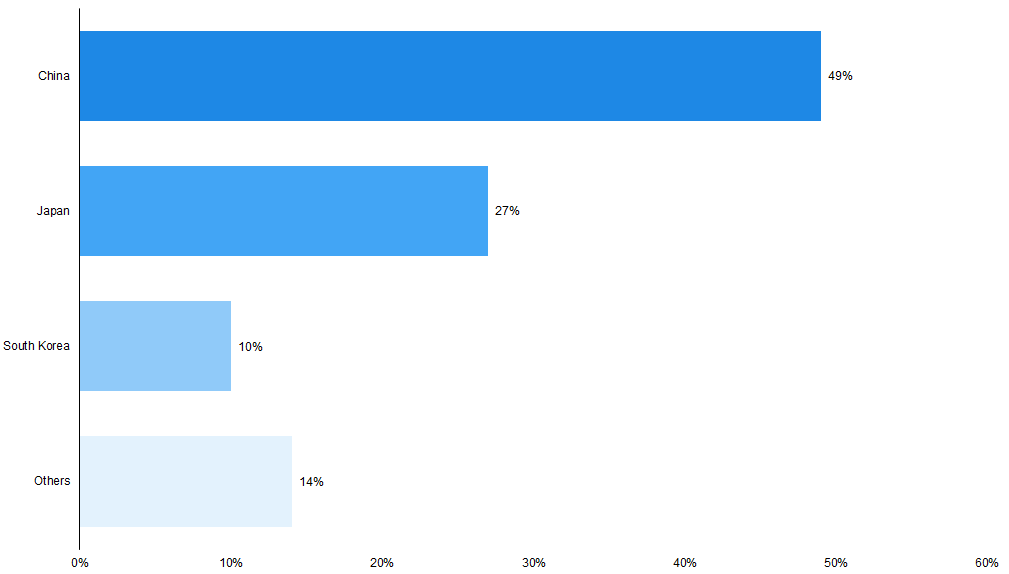
According to data gathered by Statista, the Asia-Pacific region’s global smart system services and IoT market platform is estimated to reach roughly USD 110 billion by 2023E (33.6% of the global market in 2023E), growing at a CAGR of 31.7% over 2017-23E. This growth could be driven by the adoption of Industry 4.0 and be supported by the region’s strong manufacturing base. Moreover, according to Frost & Sullivan, China is likely spearhead global industrial IoT spending and to account for 49% of it by 2020E while Japan, South Korea, and India, are also estimated to capture a considerable share of the industrial IoT market by 2020E. The bulk of the spending is estimated to be for manufacturing-related activity. |
|
Moreover, according to a survey undertaken by PwC, the Asia-Pacific region is leading digitisation: 19% of manufacturers have achieved ‘Digital Champion’ status (as per the survey methodology), compared with 11% in the Americas and 5% in EMEA. The Asia-Pacific region achieved this status based on digitisation and end-to-end integration of operations by introducing digital products and services and connecting new technologies across their organisations at a much faster rate than peers in the Americas and EMEA. This gap should continue to widen, as roughly 32% of Asian companies plan to have established mature digital ecosystems over 2017-23E, compared with about 24% in the Americas and roughly 15% in EMEA by 2023E. |
|
Moreover, according to a survey by McKinsey, 96% of businesses in ASEAN believe Industry 4.0 will introduce new business models into their industries. Nine out of ten respondents said improved performance will be one of the main benefits of new technologies. Additionally, in manufacturing-based economies such as Indonesia, Thailand, and Vietnam, respondents were generally optimistic about the prospects of Industry 4.0: more than 70% of respondents from each country said their view of Industry 4.0 had improved over the previous year. |
|
Asia-Pacific to Become the Largest Contributor to the Global Smart Systems and IoT Market by 2023 |
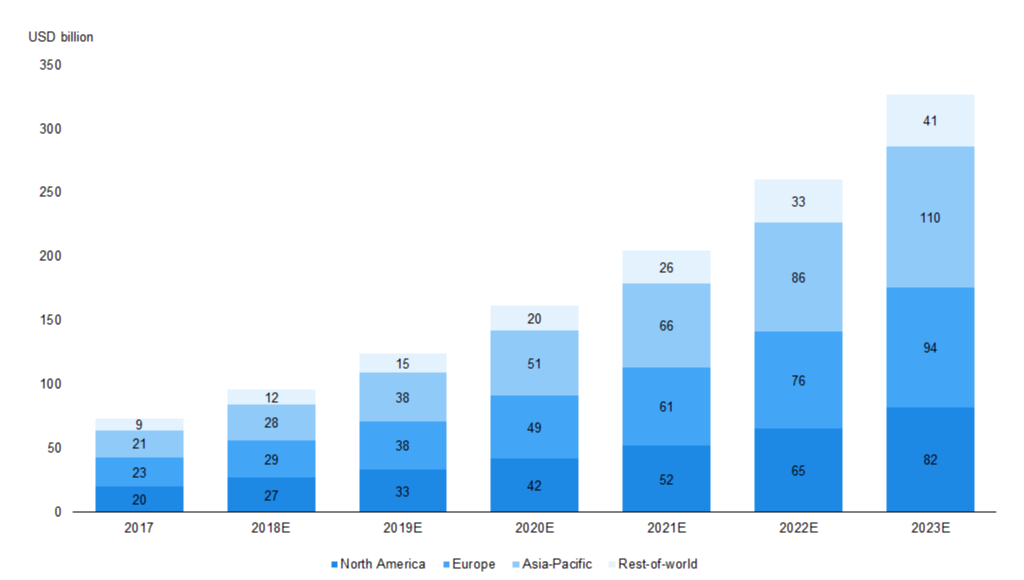 |
|
Source: Statista estimates and Harbor Research |
|
China Expected to Lead IoT Spending in Asia-Pacific by 2020 – Potentially Indicating Industry 4.0 Implementation in the Region |
 |
|
Source: Recreated by UZABASE based on Frost & Sullivan estimates |
|
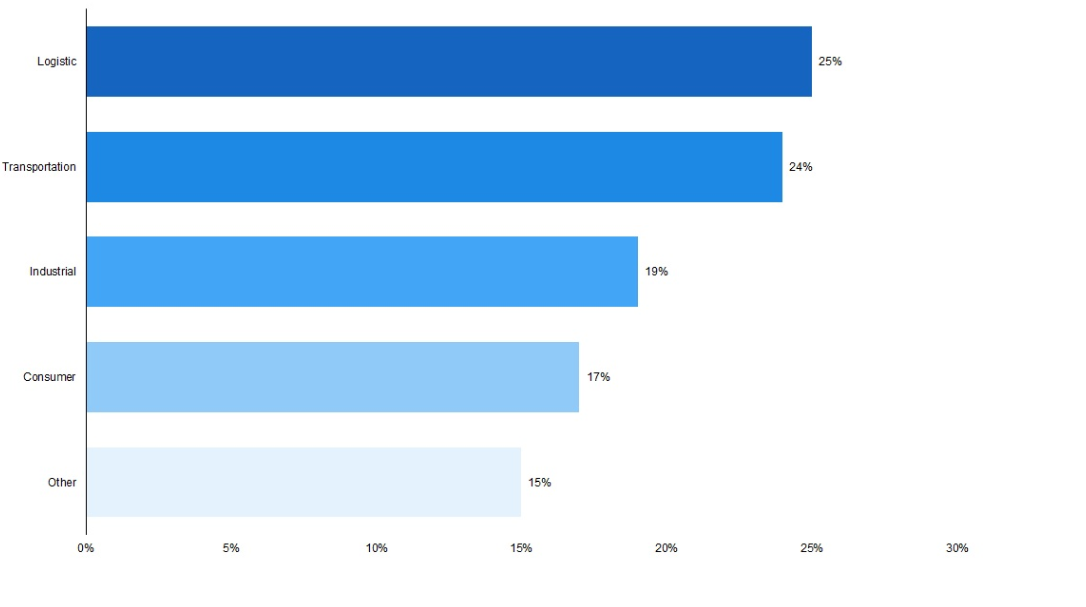
Logistics and Transportation Industry to See the Highest Level of IoT Spend in Asia-Pacific, Owing to Supply Chain Digitisation (2020E) |
 |
|
Source: Recreated by UZABASE based on Frost & Sullivan estimates |
|
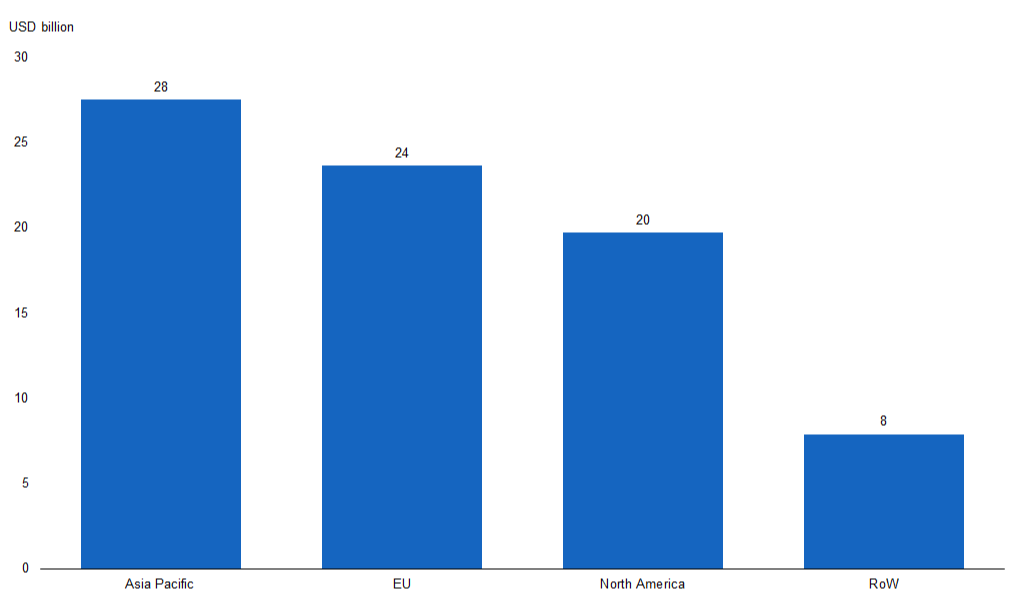
The Factory Automation Market Is Set to Be the Largest in Asia-Pacific by 2018E, with Signs of Industry 4.0 Adoption |
 |
|
Source: Statista based on HKExnews, UBS, Frost & Sullivan, and Emerson data |
|
Industry 4.0 and Cybercrime Vulnerability in Asia: Increase in Cyberattacks Could Raise Security Spend |
|
Along with the adoption of Industry 4.0 in Asia, many sources believe the region could come under heavy threat from a growing trend of cybercrime. According to McAfee and the CSIS, the East Asia and Pacific Zone was estimated to have incurred approximately USD 200 billion in cybercrime costs in 2017 (33.3% of global costs), and this is expected to increase going forward under Industry 4.0 evolution in the region. |
|
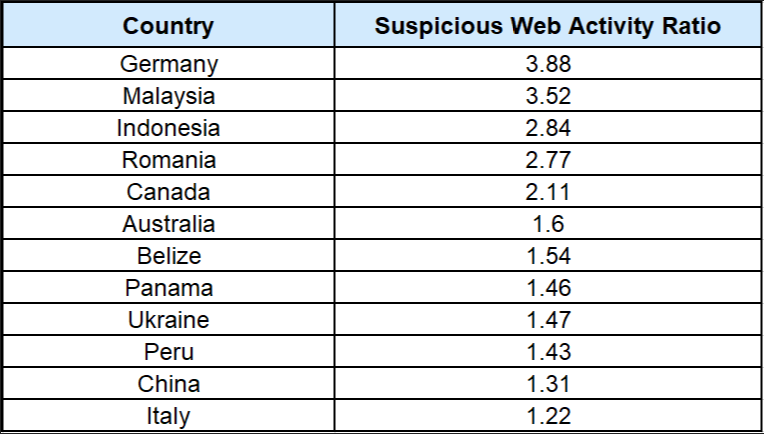
Moreover, according to a report by AT Kearney on cybersecurity, ASEAN, which is estimated to become one of the world’s top 5 digital economies globally by 2020, is also expected to be a prime target for cyberattacks. According to the report, ASEAN countries are being used as the launch site for cyberattacks due to its unsecured infrastructure, where computers can be easily infected by large-scale attacks or be used as hubs for a single point of attack to gain access to larger, global connections. Malaysia, Indonesia, and Vietnam are cited as hotspots for major blocked suspicious web activity (up to 3.5x the standard ratio). ASEAN countries are also attractive for cyberattacks by spam botnets (a form of virus or hack). For instance, Vietnam registered 1.6 million internet protocol (IP) blocks between December 2015 and November 2016; the country is in the top 5 list of countries from where attacks against IoT devices originated in 2016. Similarly, cyberattacks on leading Industry 4.0 player China have soared in the past two years. The average number of cyberattacks detected by companies in mainland China and Hong Kong grew roughly by over 900% between 2014 and 2016. According to one survey, the number of attacks averaged more than 7 a day for each of the survey’s 440 China-based respondents — around half of the global average of 13 as of 2016. |
|
Moreover, in 2017, a worldwide ‘ransomware’ cyberattack affected computers that run factories, banks, government agencies, and transport systems in Asian countries such as China, India, and Japan, among others. Chinese state media said 29,372 institutions in China had been infected, along with over 100,000 devices (consumer and industrial). In India, a terminal operated by Maersk at the Jawaharlal Nehru Port Trust (India’s biggest container port) near Mumbai was unable to load or unload because of the attack; as the Gateway Terminal India facility was unable to identify shipment ownership, the port had to clear cargo manually. In addition, India-based employees at Beiersdorf (makers of Nivea skincare products) and Reckitt Benckiser (which owns Enfamil and Lysol) also stated that the attack had impacted some of their production and distribution systems in the country. |
|
Against this back drop of a growing cyberattack threat in the region, there is expected to be a rise in security spending over the coming years. According to A.T Kearney, the ASEAN region’s security spend is estimated to increase at a CAGR of 15% over 2015-25E, with Vietnam and Philippines spending expected to grow the fastest. |
|
Suspicious Web Activity Relatively High in Asia; Could Increase Alongside Industry 4.0 |
 |
|
Source: Recreated by UZABASE based on AT Kearney and Cisco data |
|
Top Ten Countries of Origin of Hacking Attacks, Based on Global Percentage of Attack Traffic (2016) |
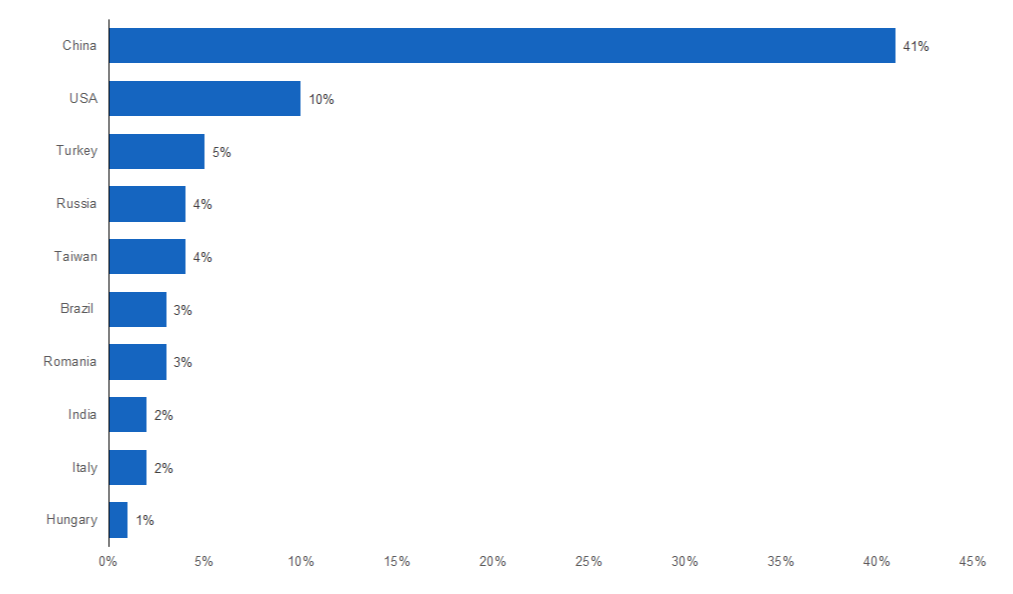 |
|
Source: Cyware |
|
Cyber Security Spend in ASEAN to Post Double-Digit Growth over 2015¬–25E |
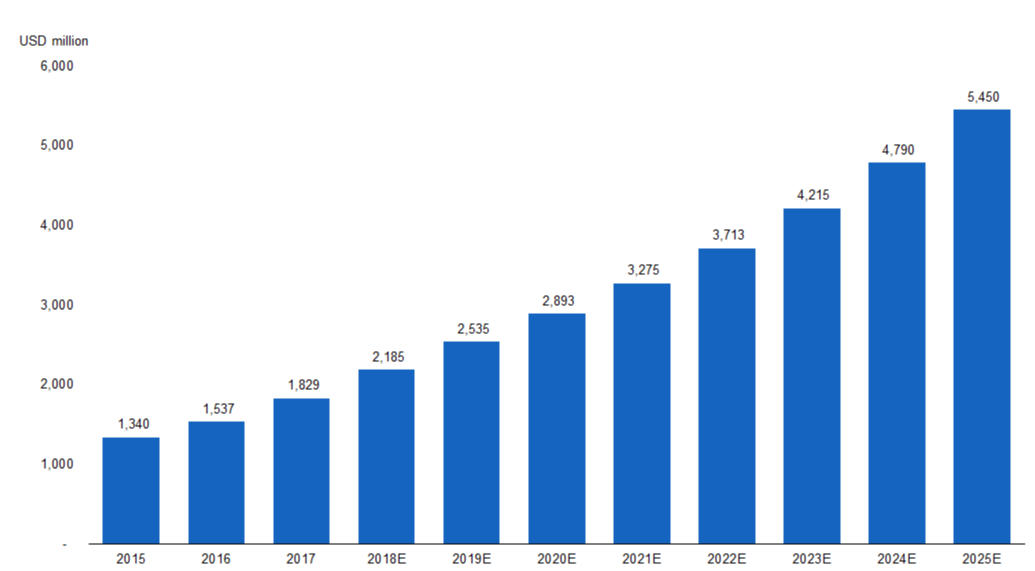 |
|
Source: AT Kearney |
|
Singapore to Remain as the Largest Contributor to Cyber Security Spend by 2025E |
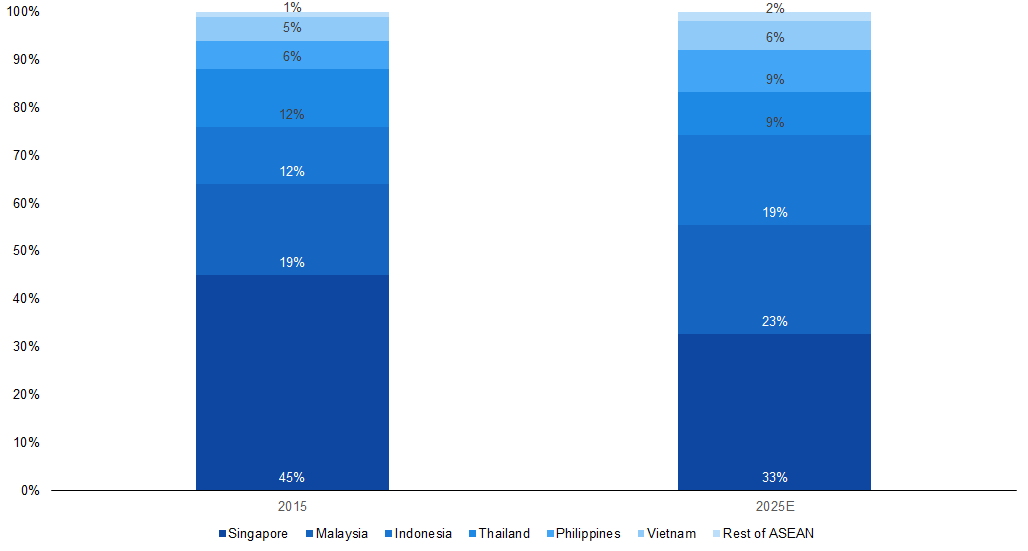 |
|
Source: AT Kearney |
 |
|
UZABASE Take: Information Security Firms that Provide Complete Solutions Should Benefit the Most from Growing Threat of Cyberattacks in Industry 4.0 |
|
There is no doubt that the Industry 4.0 revolution is taking place, and there is no going back. We believe that information security providers (who help organisations adopt processes such as digital supply chains and smart factories) are the industry that could see significant growth alongside Industry 4.0. However, given the pace of growth in Industry 4.0 and its complexity, along with growing cybercrime, security solution companies need to evolve faster in order to tackle external threats. |
|
According to various sources, the Asia-Pacific IoT security market is estimated to grow at a CAGR of 38.4% over 2017¬–23E; this should be mainly driven by the need for security services for IoT-powered business activities such as supply chains and smart factories This is in line with estimated growth in Industry 4.0 at a CAGR of about 14.7% over 2017–22E to about USD 152 billion. |
|
Moreover, we believe that the region with the highest potential for providing information security services is Asia. This is backed by multiple sources that expect the Asian region (especially China, South Korea, Japan, and India) to hold the largest share of the Industry 4.0 market. Moreover, we believe that the IoT security market in China — where most of the Industry 4.0 implementations are taking place — is set to experience the fastest growth in the Asia-Pacific region, followed by Japan, driven by the adoption of identity and access management (IAM – the security and business discipline that enables the right individuals to access the right resources at the right times and for the right reasons). |
|
The Asian IoT security market has many players, a few of whom are relatively large. Security players such as Cisco, McAfee, IBM, Oracle, Symantec Corp., FireEye, Honeywell, and Gemalto (in Asia as well) have acquired most of the market. In our view, market competition could grow in the next 3–5 years, as many SMEs are likely to enter the market with strong portfolios, challenging existing big security players. Moreover, we believe M&As are likely to play a major role as small companies are targeted by larger cybersecurity organisations. Although the market is currently dominated by large companies, its scope remains attractive, offering opportunities for small players to create brand value and gain market share. |
|
Security Companies That Stand to Benefit from Demand for Cyber Solutions Under Industry 4.0 |
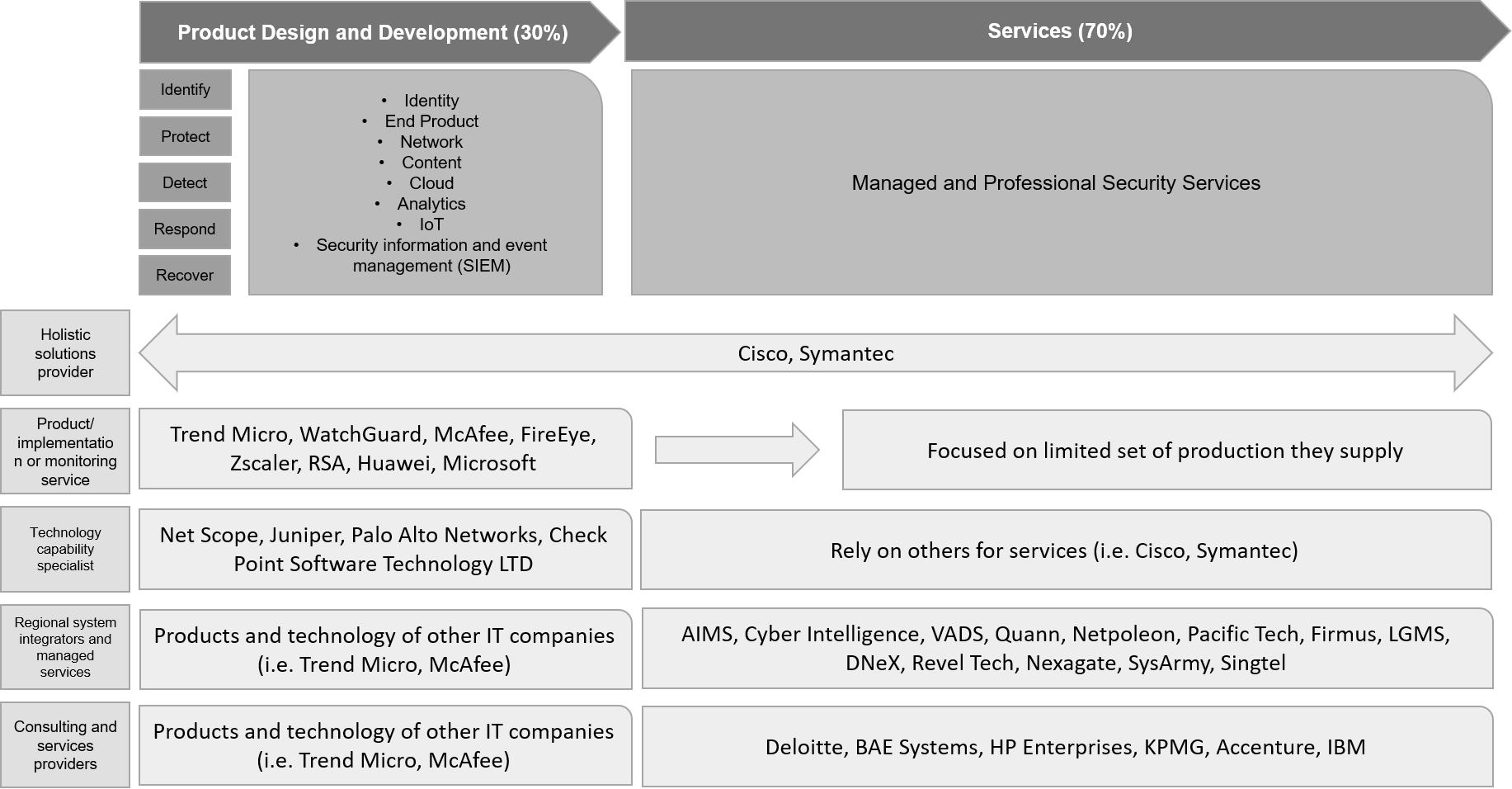 |
|
Source: Recreated by UZABASE based on AT Kearney dataNote: This list is only for illustration purposes and is non-exhaustive |
Appendix |
|
Growing Threat of Cybercrime: The Third-Largest Form of Crime Globally |
|
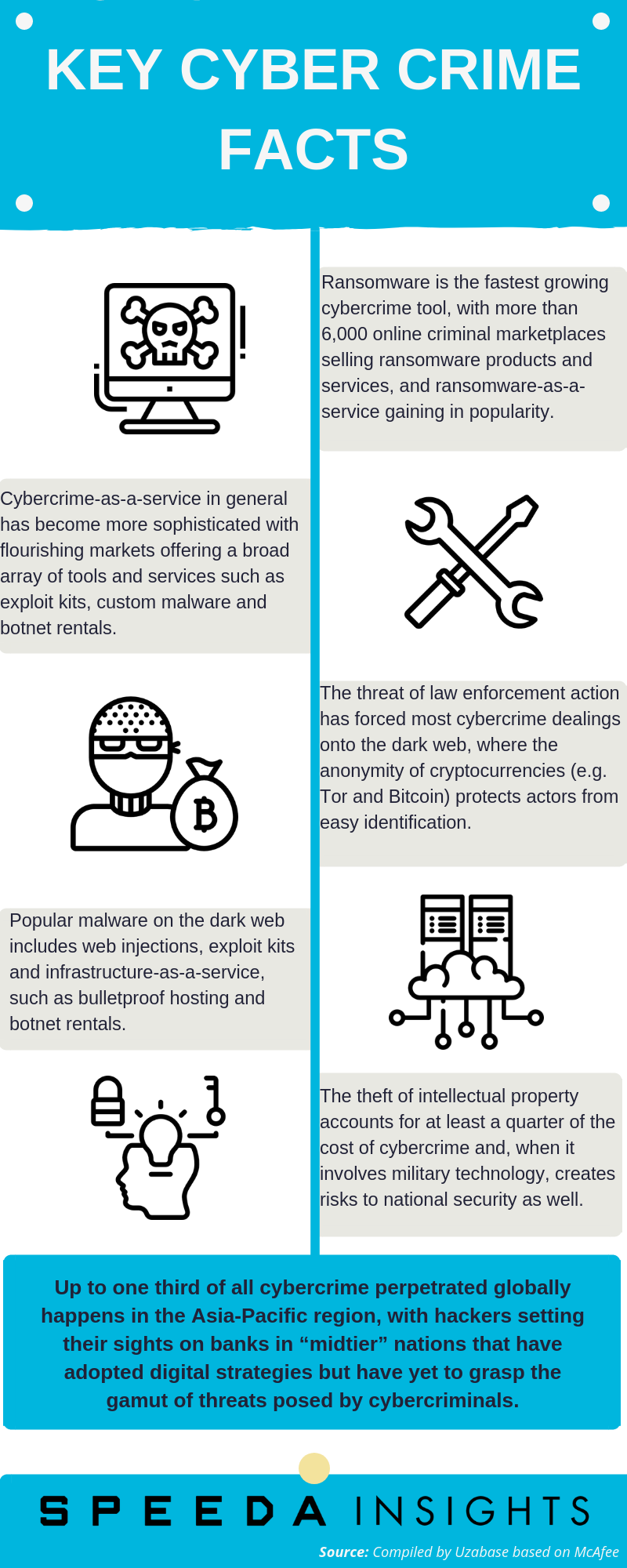
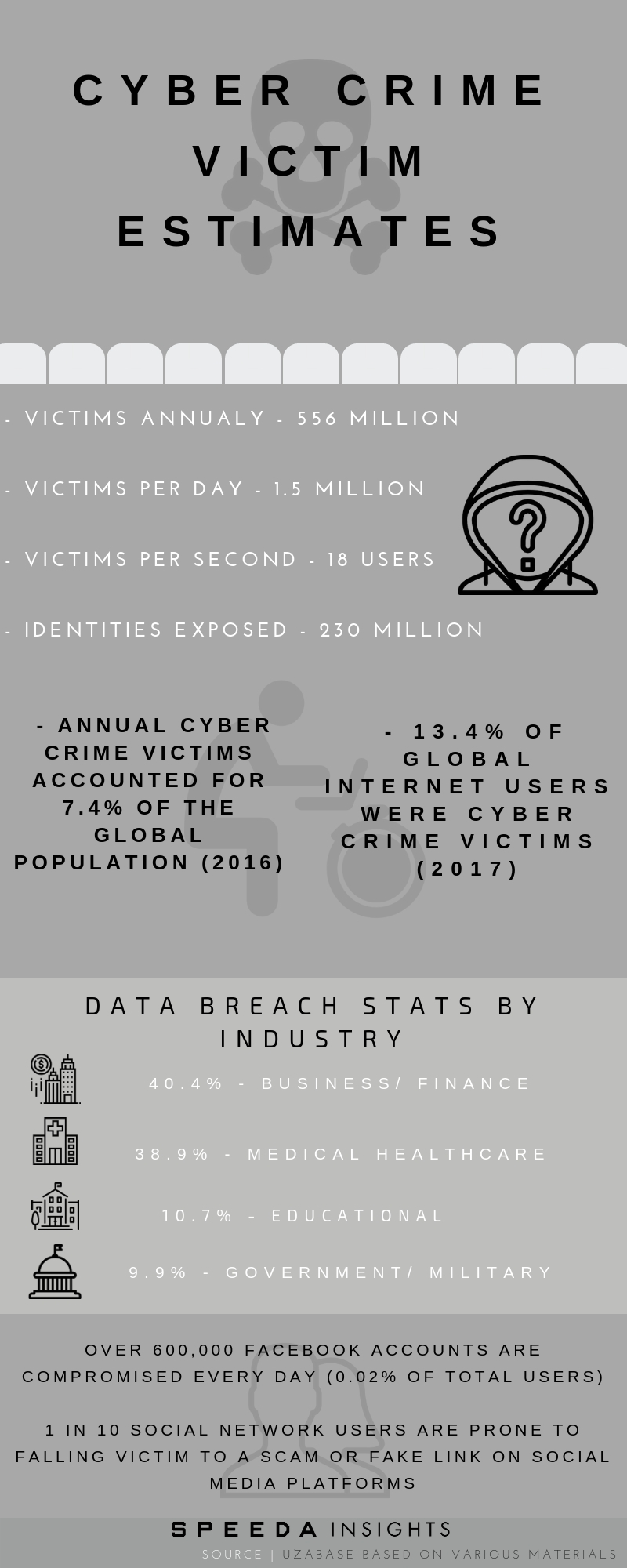
Global cybercrime costs accumulated to roughly USD 600 billion in 2017, or 0.8% of global GDP that year, according to the Centre for Strategic and International Studies (CSIS) and online security company McAfee. Looking at cybercrime in terms of the global internet economy (USD 4.2 trillion in 2016), cybercrime was viewed as a 14% hindrance on growth on a yearly basis, as per McAfee. Cybercrime caused about USD 171 billion in damages in the Asia-Pacific region (accounting for 28.5% of global cybercrime costs in 2017), according to a study by the CSIS and McAfee. The study also found that various locations in Southeast Asia had already been used as launch sites for cyberattacks. The region presents “vulnerable hotbeds of unsecured infrastructure”, where computers can either be infected easily by large-scale attacks or provide well-connected hubs from which to initiate them. McAfee also reported that cybercrimes ranked as the third-largest form of global crime, behind government corruption and narcotics. |
|
Wealthier countries tend to incur higher cybercrime costs. However, those that experience the worst losses (from cybercrime) as a percentage of national income are mid-tier nations that have been digitised but are not yet fully capable in cybersecurity (e.g. Vietnam, the Philippines). |
 |
 |
|
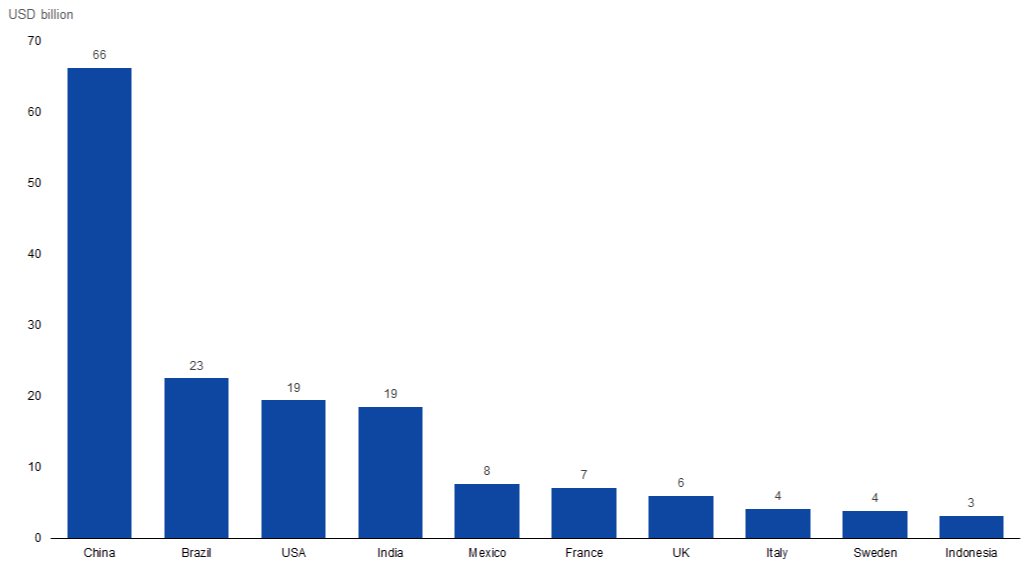
Consumer Cost Due to Cybercrime — Top 10 Countries Accounted for Nearly 30% of Global Cybercrime Costs (2017) |
 |
|
Source: Statista based on Norton Cyber Security Insight Report |
|
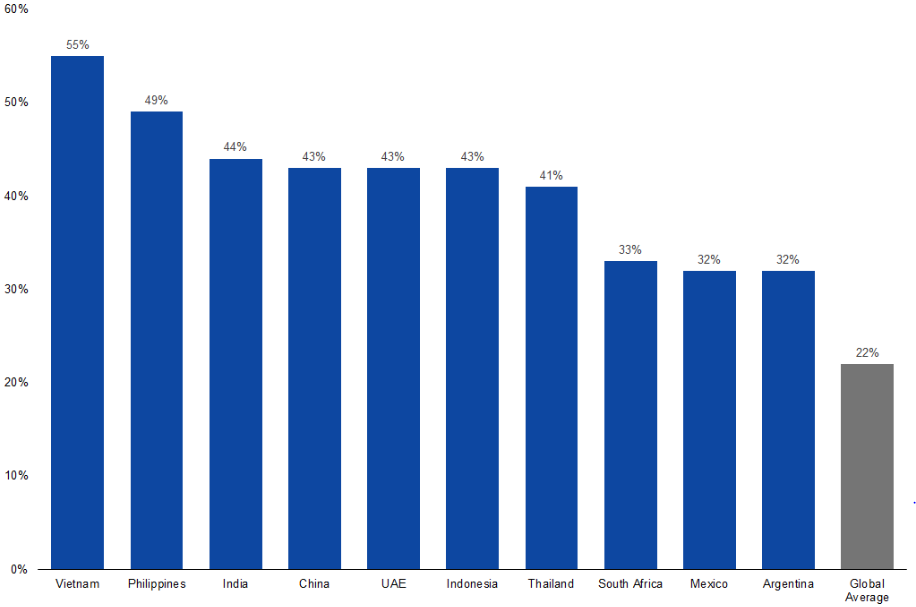
Percentage of Internet Users Who Encountered Cyberthreats (Selected Countries; 2H2017) |
 |
|
Source: Statista based on Kaspersky Lab Online Survey |
|
Digital Supply Network to Increase Cyber Risks |
|
Supply chains — along which materials enter production processes and semi- or fully finished goods are distributed — are fundamental to any manufacturing organisation. They are also tightly connected to consumer demand: many global organisations use demand forecasts to determine the quantity of materials needed, manufacturing line requirements, and distribution channel loads. |
|
The emergence of Industry 4.0 technologies is expected to prompt further evolution in the traditional linear supply-chain structure by introducing intelligent, connected platforms and devices across the value chain. This should result in a digital supply network (DSN) capable of capturing data from points across the value chain to inform each other. The result could be better management and flow of materials and goods, more efficient use of resources, and supplies that more appropriately meet customer needs. For all its benefits, however, the increasing interconnectedness of the DSN also brings with it cyber weaknesses that should be properly planned for and accounted for at every stage, from design through operation, in order to curb significant risks. |
|
Cyberattacks against digital supply chains have recently been on the rise. Attacks on supply chains typically seek to introduce security flaws or exploitable features into hardware, software, or digital services, which are then passed on to customers. Notable examples of supply chain attacks from 2017 include the compromise of managed service providers (MSPs) and of several software products. Suspected Chinese hackers compromised several global MSPs that year that deliver outsourced IT, HR, and business services. It is believed that the attackers obtained commercially sensitive data (i.e. financial data, personal information, etc.) from the MSPs and their clients, including government agencies. According to the National Cyber Security Centre (NCSC), MSPs represent a particularly attractive target, as they link to thousands of customers worldwide. Even if a client has strong cybersecurity measures in place, they might find themselves vulnerable if a trusted network link to an MSP is compromised. In 2016, the industry saw many supply chain cyberattacks targeting software. Between 15 August and 12 September 2017, downloads of a free computer clean-up tool known as “CCleaner” were infected with malware. The incident is believed to have affected over 2 million downloads by individuals and businesses, resulting in further attacks against large technology and telecommunications companies in the UK, Taiwan, Japan, Germany, and the USA. |
|
NotPetya, the global malware attack that caused major disruptions in June 2017, was also a supply-chain cyberattack. Attackers introduced the malware into MeDoc, a legitimate software application widely used by businesses in Ukraine for handling tax returns. The compromised MeDoc update infected users of the application, and the malware spread through the networks. |
|
Supply-chain cyberattacks are an increasing threat for cybersecurity agencies and firms. Symantec’s analysis identified a 200% increase (in 2017) in attacks involving hackers injected malware into the software supply chain. This equates to one attack every month in 2017, compared with four attacks in all of 2016. |
|
Smart Factories Face New Cyber Risks in Age of Smart Production |
|
Modern industrial control systems (ICSs) allow engineers to rely increasingly on automation while maintaining high efficiency and resource control via connected systems (e.g. ERP, manufacturing execution, and supervisory control and data acquisition systems). These connections can often streamline processes and make operations smoother and more efficient, but increased networking and usage of commercial, off-the-shelf products introduce a variety of points of exposure to cybersecurity risks. |
|
Almost any connected device, whether in an automated system on a shop floor or remotely located at a third-party contract manufacturer, should be considered a risk. This includes devices that only peripherally or indirectly touch the production process. Misused or manipulated requests for ad hoc production lines can result in financial loss, low product quality, and even safety concerns for workers. Connected factories could also be vulnerable to shutdowns or other types of attacks. As Industry 4.0 progresses, the potential impacts could become broader and more significant. Yet many manufacturers remain unprepared: a 2016 study by Deloitte and MAPI found that one-third of manufacturers have never performed any cyber-risk assessments of the ICSs operating on their factory floors. |
|
As production systems grow ever more connected, cyberthreats increase and broaden beyond those seen in the DSN. From an operational perspective, modern ICS environments allow engineers to deploy unmanned sites while maintaining high efficiency and resource control. They do so by using the connected systems mentioned previously. These connected systems can often streamline processes and make things easier and more efficient, and they have continued to evolve, becoming increasingly more automated and autonomous. |
|
Increase in Connected Objects to Keep Industry Vulnerable |
|
Today’s products are connected not just to each other, but also increasingly to even the manufacturer and the supply network. Therefore, cyber risk no longer ends once the product is sold. By 2020E, it is estimated that more than 20 billion IoT devices will be deployed around the world. Many of them will have dedicated mobile apps that connect the user with either manufacturer or a service provider. |
|
Compromised IoT devices at production facilities can lead to downtime, damage to equipment or facilities, or even loss of life. Monetary losses are also possible in the form of fines, litigation expenses, and revenue loss due to brand damage. Current approaches to safeguarding connected objects could prove insufficient, and it is becoming increasingly difficult to find the highly skilled cybersecurity talent required. Taken together, these trends highlight the need for IoT device manufacturers to produce security-hardened devices by incorporating stronger, more secure software development practices. Of the more than 20 billion IoT devices estimated to be deployed around the world by 2020E, many might find their way into manufacturing facilities and production lines; however, many others are expected to enter the marketplace, where customers, whether B2B or B2C, can purchase and use them. |
|
The 2016 Deloitte-MAPI survey noted that close to half of manufacturers use mobile apps for connected products, while three-quarters use Wi-Fi networks to transmit data to and from connected products. The use of these types of avenues for connectivity often open up considerable vulnerabilities. IoT device manufacturers should therefore consider incorporating stronger, more secure software development practices into existing IoT development life cycles to address the significant cyber risk these devices often present — this could prove challenging. Expecting consumers to update security settings, apply effective security countermeasures, update device firmware, or even change default device passwords has often proven unsuccessful. A distributed denial of service (DDoS) attack on the IoT in October 2016 via the malware Mirai showed how attackers could leverage these weaknesses. In the attack, a virus infected consumer IoT devices such as connected cameras and televisions and turned them into botnets, bombarding servers with traffic until they collapsed and impeding access to multiple popular websites across the USA for the better part of a day. Researchers identified that the compromised devices used to conduct the DDoS attack were secured with vendor default passwords and had not received required security patches or updates. It should be noted that some vendor passwords were hard-coded into the device firmware, and the vendors offered users no mechanism to change those passwords. Existing industrial production facilities often lack the security sophistication and infrastructure to detect and counter such attacks once they break through the perimeter protection. |



